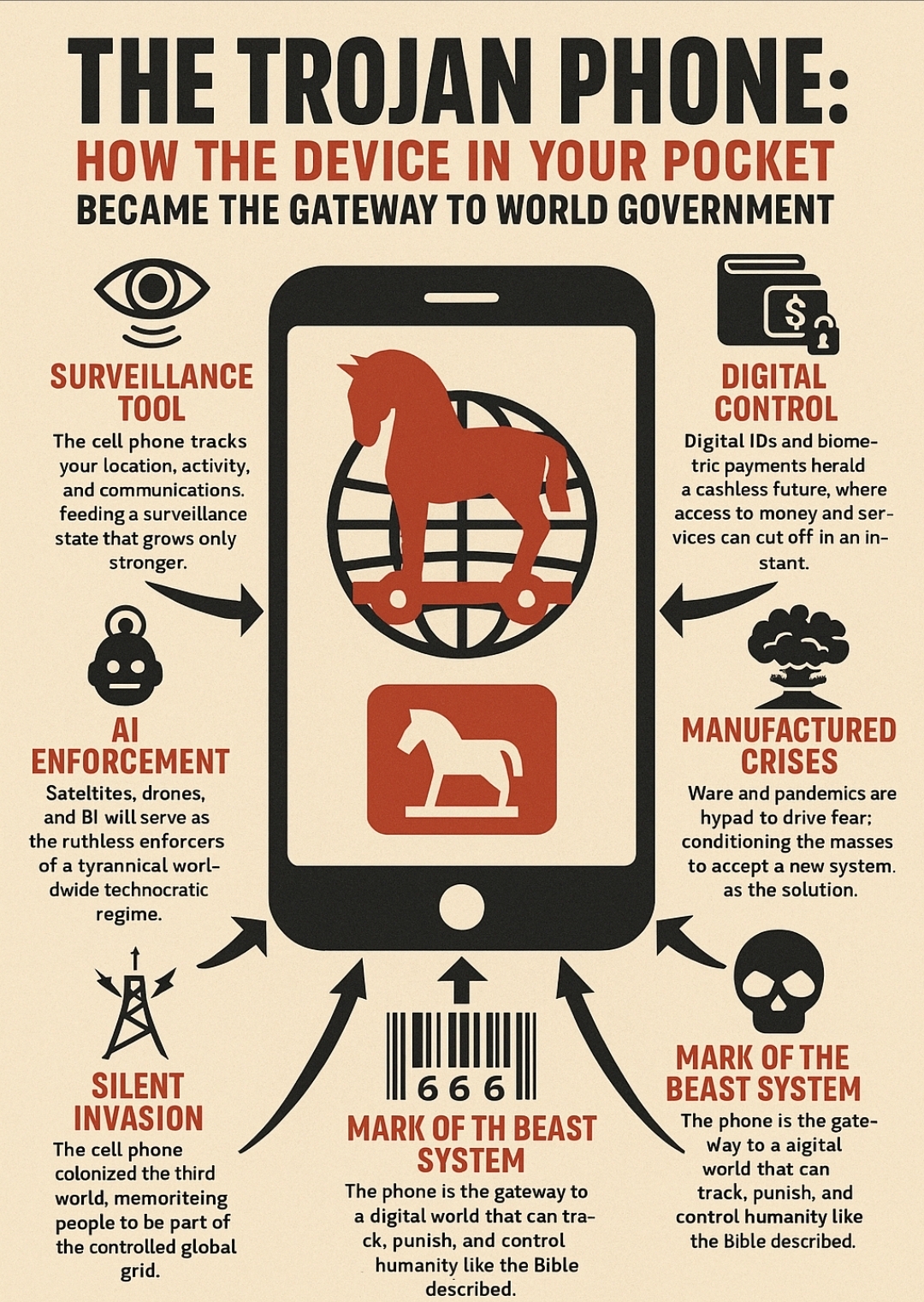
In ancient myth, the Trojans welcomed a beautiful wooden horse into their city—believing it was a gift—only to discover it was filled with soldiers who would destroy them from within. Today, the same story is playing out in real time. The wooden horse has been replaced by a sleek, glowing device: the cell phone. And the soldiers hidden inside are surveillance systems, corporate algorithms, AI enforcement mechanisms, and a web of interconnected laws and data pipelines that—together—build the foundation for a world government.
The Smart Rifle in Your Pocket
From the moment smartphones hit the market, they were sold as tools of empowerment—maps, instant communication, a camera in your hand. But like a smart rifle, their precision isn’t limited to your benefit; it’s also weaponized against you.
- Geo-tracking lets governments and corporations know where you are at all times.
- Behavioral analytics predict what you’ll do next.
- Real-time content control can silence you, redirect your thinking, or nudge your decisions—without you realizing.
Every “free” app is a cartridge in the chamber. Every update is a new scope that makes the shot more accurate. The target? Your autonomy.
The Digital Sword and the Beast System
In biblical prophecy, the “Mark of the Beast” is tied to commerce, allegiance, and control—no one can buy or sell without it. Your phone is already that mark in embryo form.
- Digital IDs are merging with payment systems.
- Facial recognition is replacing cash and cards.
- QR codes, biometric scans, and mobile wallets make the device a gatekeeper to economic participation.
What was once a communication tool is now the sword that can sever you from the marketplace if your behavior doesn’t align with the system’s rules.
The Silent Invasion – How the Cell Phone Colonized the Developing World
The infiltration of cell phones into third-world and developing nations was no accident of market forces — it was a carefully engineered strategy. On the surface, it was framed as a humanitarian gift: “connecting the unconnected,” “bridging the digital divide,” and “bringing opportunity to every corner of the globe.” In reality, it was a calculated step in binding billions into a single, monitored, programmable network — the digital nervous system of a coming world government.
The False Humanitarian Narrative
Western governments, NGOs, and tech corporations worked hand-in-hand to subsidize mobile infrastructure in poor nations. The pitch was irresistible: better communication for farmers, small businesses, and families. But the unspoken truth was that this “gift” was also the hook — once people adopted the device, they were drawn into the same global grid of surveillance, behavioral data mining, and algorithmic influence that already ensnared the developed world.
The Leapfrogging Trap
By skipping traditional infrastructure (landlines, wired internet), these nations became instantly dependent on a wireless, corporate-controlled backbone. The leapfrogging from no connectivity straight to smartphones meant no period of decentralized communication infrastructure — no independent networks to defend. From the moment they came online, they were plugged directly into global cloud servers owned by the same handful of Big Tech oligarchs.
The “Freedom” Illusion
The cell phone was marketed as the tool of empowerment — giving farmers real-time crop prices, students access to online education, and activists a voice on the world stage. But the same device that offered information also harvested it. Every call, every location ping, every keystroke became part of a profile — feeding into AI models that could predict and shape the population’s behavior. In effect, the so-called “freedom” was a digitized cage.
Embedding in Daily Life
Cheap smartphones and data plans — often subsidized by the very organizations that claim to fight inequality — ensured mass adoption. Digital payment systems, ID verification apps, and “free” social media became the glue of the new dependency. In short order, life without a phone became nearly impossible — an intentional design to make opting out unthinkable.
The Final Merge – Digital Identity as Citizenship
Once the developing world was locked in, the next phase became clear: digital ID. The same device used to connect with family or check market prices became the portal for proving one’s identity, accessing aid, and participating in commerce. Lose your phone or fall foul of the system, and you risk losing your ability to function in society. This is not connection — it is quiet annexation.
World Rollout
The rollout of cell phones in third-world countries was not just about connecting people — it was about mapping them, memorizing them, and integrating them into a unified, surveilled network. From the first subsidized handset to the mandatory digital ID, the path was clear: prepare every nation, rich or poor, to be plugged into the infrastructure of a single, centralized world government.
The Hijacked Mind: From Cool to Control (1997–2030)
The first generation of mobile devices sold cool. The next generation sold connection. The current generation sells compliance.
- In the late 1990s and early 2000s, pop culture made mobile devices a status symbol.
- By the 2010s, social media rewired dopamine pathways, making phones the primary source of identity and self-worth.
- By the 2020s, the device became essential for “proof of life” in the system—vaccination records, travel passes, and political conformity all funneled through the same screen.
The cool factor was the bait. The control factor is the hook. And the global governance factor is the reel.
Global Collaboration: Building the Infrastructure
No single government or company could achieve this alone. The integration of cell phones into a one-world system requires synchronized cooperation:
- Big Tech builds the hardware and platforms.
- Global finance integrates payment rails.
- International law harmonizes data-sharing agreements.
- Military and intelligence agencies ensure the system’s resilience against resistance.
From NATO’s cyber warfare divisions to UN-backed “digital inclusion” initiatives, the scaffolding for a unified control grid is nearly complete.
War and Fear as the Accelerant
Conflict—whether physical or economic—has always been the fastest way to centralize control. Global crises create the “emergency” atmosphere that justifies new digital regulations.
- In war, phones become both lifelines and locators.
- Fear of cyberattacks justifies tighter controls over online speech and encryption.
- Economic instability pressures populations into accepting centralized digital currencies accessible only via approved devices.
The Trojan phone thrives in chaos; it grows stronger when people cling to it for security.
AI as the Enforcement Mechanism
Once the infrastructure is in place, the real enforcer isn’t a human dictator—it’s an algorithm.
- AI policing of online speech.
- Automated financial sanctions for dissenters.
- Predictive behavior monitoring that can preemptively lock you out before you act.
This is the ultimate spiritual test: a system so seamless, so embedded in daily life, that refusing it means voluntary exile from commerce, travel, and connection.
Conclusion: The Trojan Horse Has Already Entered the Gates
Most people still think they’re holding a phone. They’re holding the master key to their own submission. And the beauty of the design is that no one forced them to take it—they paid for it, upgraded it, and bragged about it on social media.
The world government’s most powerful weapon isn’t a tank, a missile, or even a law. It’s the glowing rectangle in your pocket. The sooner we recognize that, the sooner we can decide whether to be willing participants in its final act—or to step outside its gates before they close for good.